With continued technological advances, there has been an increase in company data being electronically entered, stored, and potentially compromised. According to the IBM 2020 Cost of Data Breach Study (sponsored by IBM Security and conducted by the Ponemon Institute), the average financial impact of a data breach for an organization in the US is $8.64 million. Unauthorized access to corporate resources poses a significant risk to organizations and can take many forms: loss of data or Intellectual Property, compliance issues like HIPAA or PCI, loss of confidence in the marketplace, and many others.
Protecting your organization from unauthorized access is critical. Simply relying on passwords is proving ineffective against the modern adversary. Stolen or weak credentials are leveraged in 80% of attacks on organizations today. Fortunately, Two Factor Authentication (2FA) supplies a method to help protect your organization from these attacks.
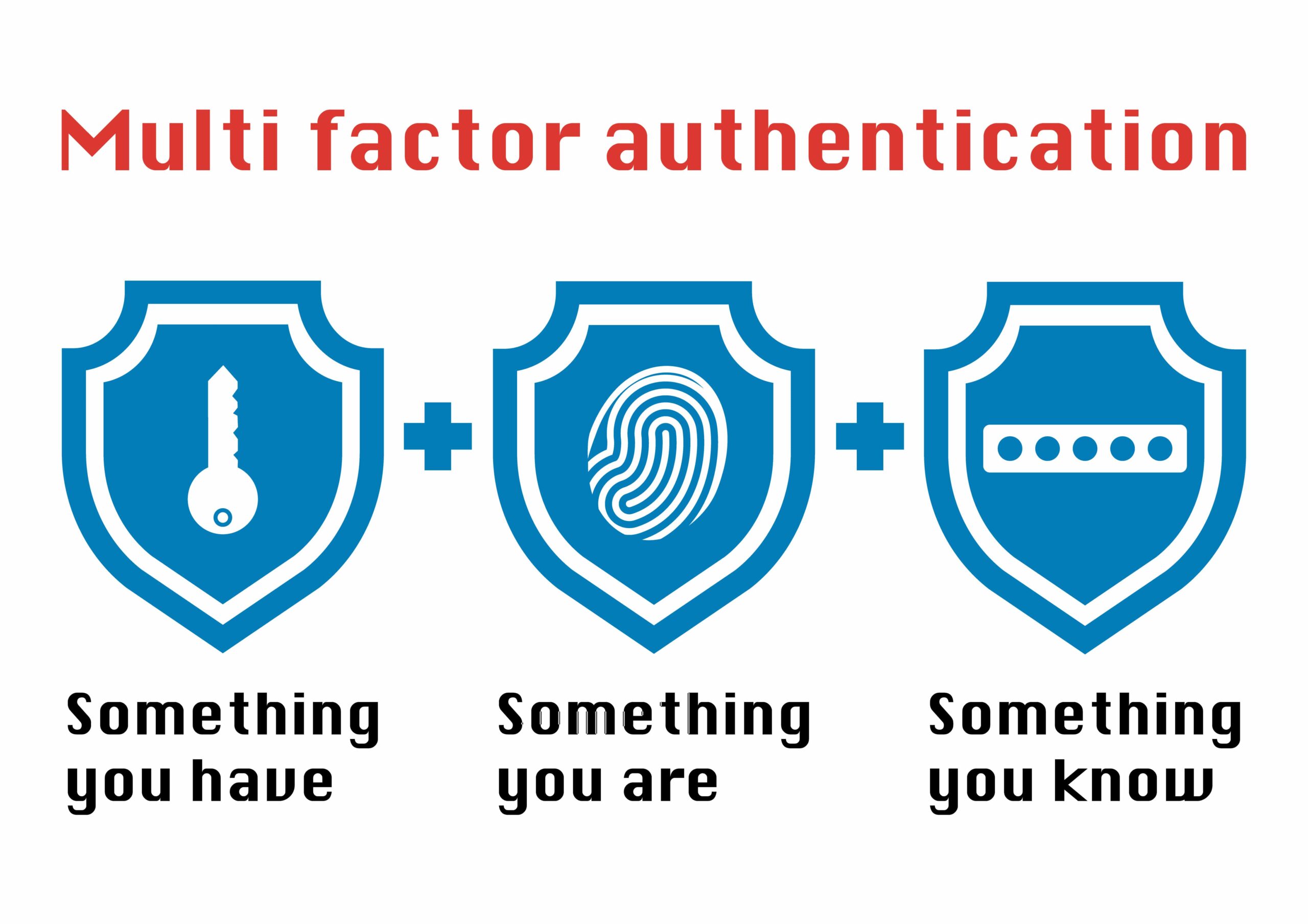
What is Two-Factor Authentication?
Two Factor Authentication combines something you know, such as a password, with something you have. The something you have in this case could be any number of things, from a security token, a phone number, a particular cell phone, a fingerprint, a retina scan, etc. In this way, a malicious actor on the other side of the world could have your password, but without access to the 2nd factor, it is useless.
How to get 2FA rolling
Step 1: Planning
A company’s executive and IT staff should first determine how their employees and customers typically gain access to data. By deciding the level of security needed for specific company information, individual 2FA methods can be implemented to best fit a company’s objectives. To do this effectively, review systems and processes to identify where 2FA can be applied, where it cannot, and what other controls need to be used, if necessary. Successful implementations of 2FA will take time. Prioritizing critical systems and workflows will provide the best return.
Step 2: Technical implementation
2FA can be used to protect VPN access, Online services, web portals, and internal services. Implementing 2FA on these applications can have differing complexities or requirements. Using the system prioritization established in step 1, your IT team should focus on protecting critical systems first.
Step 3: System rollout and training
Many 2FA implementations are available that minimize the impact to workflow and employee experience. Form a plan to introduce this change to the employees to make the transition to 2FA as smooth as possible. Support from leadership is critical at this stage to communicate the importance of security to the staff. Ongoing training and documentation should also be made available as new staff or systems get added.
Step 4: Maintenance
As the need for 2FA has become clearer, more systems and service providers are adding support. Like much of security, 2FA implementation is never done. Unsupported applications and systems should be reviewed on a regular basis to see if enabling 2FA is a possibility to keep your organization safe.
How WIN can help
Here at WIN, we can help your company with any of the above steps. Our team can plan, implement, and support your solution. We know how to match a security solution to your business goals. Do not let a data breach occur within your organization. Let WIN help you develop a preemptive, cost–effective plan to secure your data.
