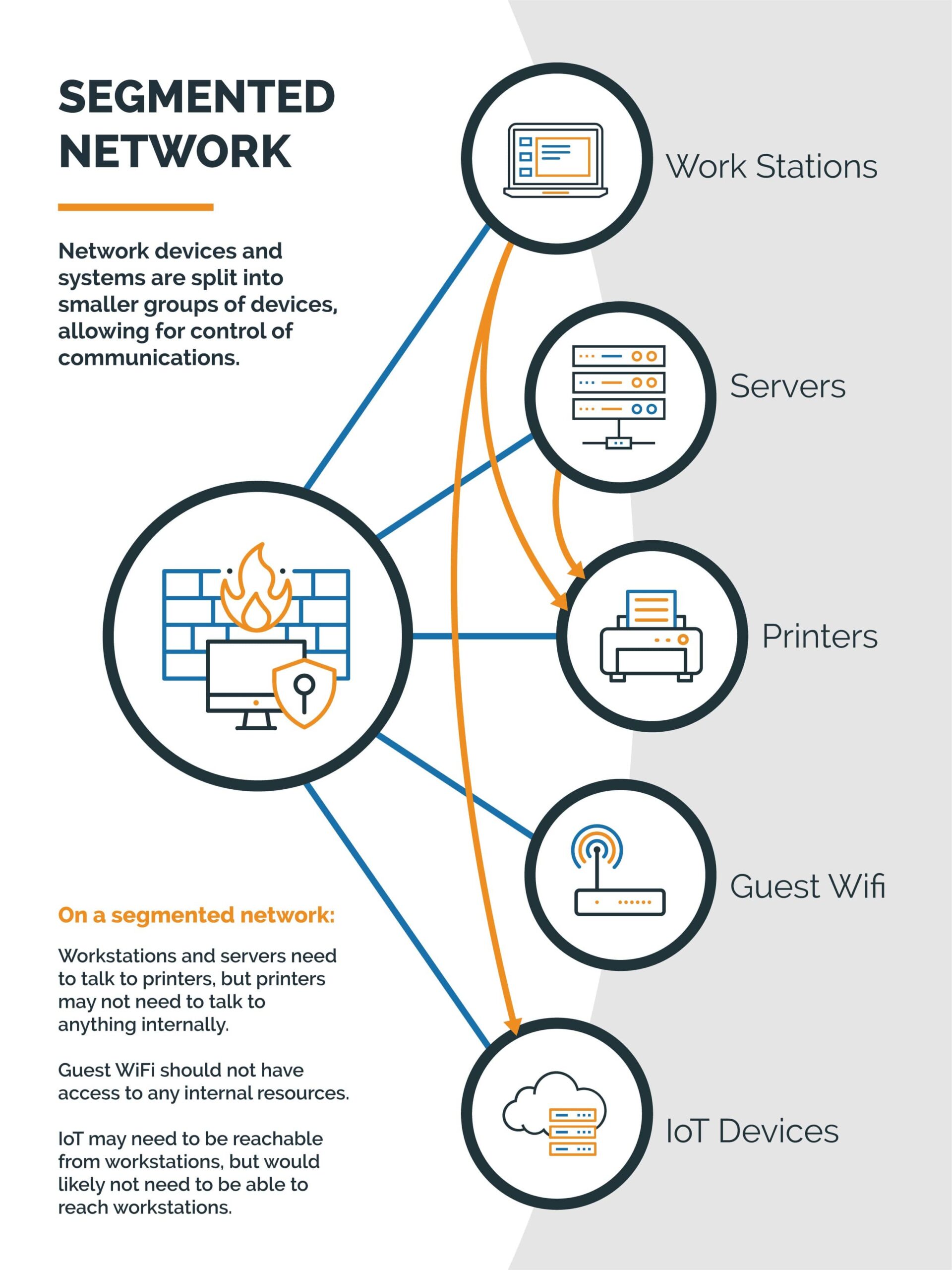
What is Network Segmentation?
Network Segmentation is a configuration in which network and computer systems inside of a corporate network are divided into logical segments. These segments typically group devices with similar purposes together for a number of performance or security reasons.
How Network Segmentation Protects your Network
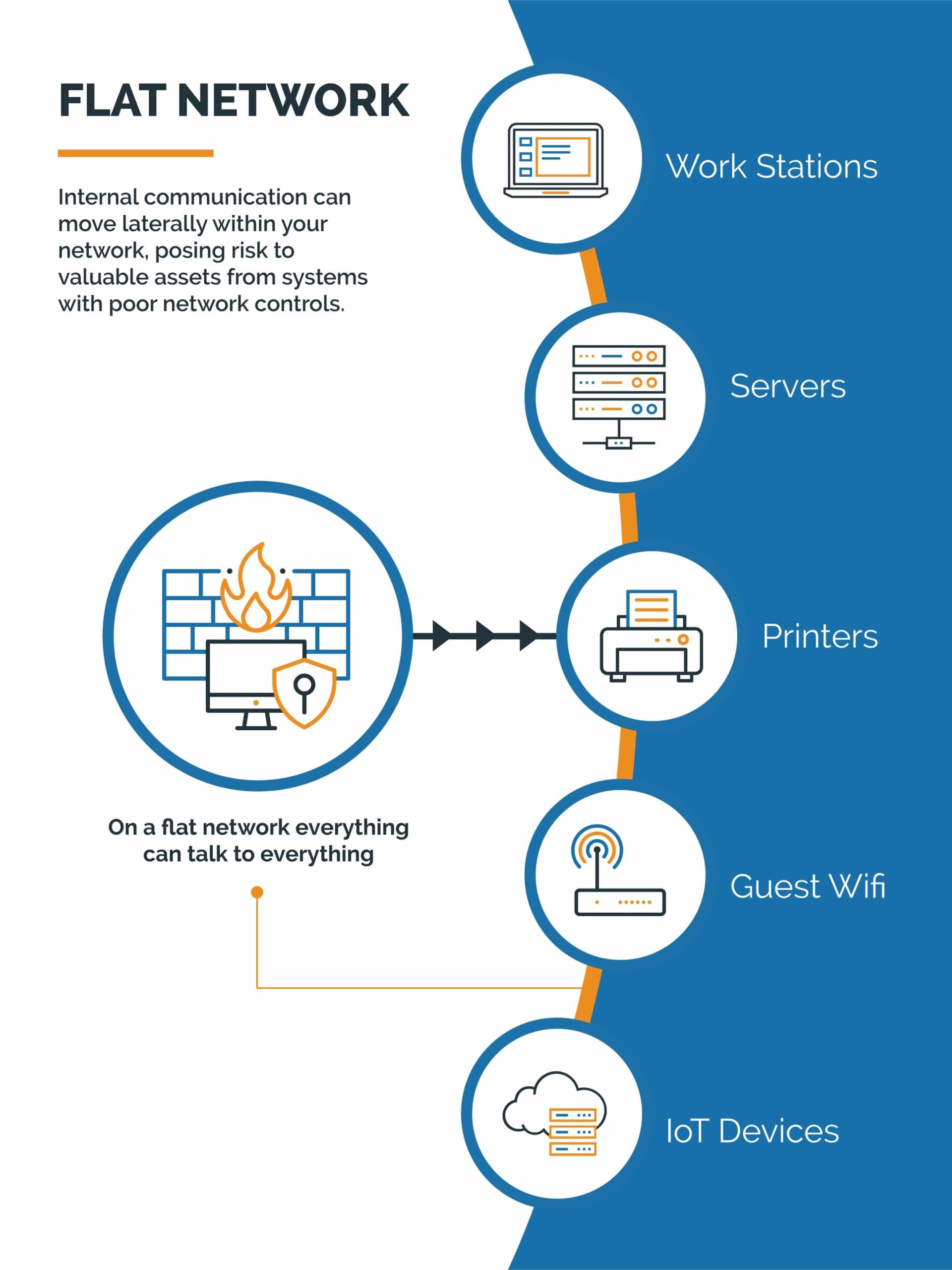
It used to be that organizations could trust the edge firewall to secure the organization from malicious actors. In this simpler time, the firewall was hardened to limit all externally sourced communication. Internal communication was considered trusted and would be allowed to pass around the network freely. The external communication is called North-South traffic and is best described as traffic that would go in and out of your network. Internal communication is commonly called East-West traffic and is best described as traffic that that moves laterally within your network.
Unfortunately, as Malicious Actors have gotten more sophisticated, so have their attacks. It is commonplace for them to compromise a system within a network, and then pivot from that system to other systems in the environment that contain a more valuable payload. Malicious Actors take advantage of the legacy trust of Internal East/West traffic to move around without difficulty or detection.
Network Segmentation helps prevent this kind of activity by forcing traffic through the corporate firewall, treating East-West traffic more like North-South communication, permitting only known and needed communications. This approach is also very helpful as many systems inside of your network have poor or unknown security controls. For example, printers or building control systems have notoriously poor security practices, are not patched often, and are easily overlooked in audits. But systems like these also do not need access to all the internal servers that exist inside of the environment. With network segmentation, it is possible to control and explicitly permit only the traffic that is needed, and block everything else. en pivot from that system to other systems in the environment that contain a more valuable payload. Malicious Actors take advantage of the legacy trust of Internal East-West traffic to move around without difficulty or detection.
Network Segmentation has other benefits as well. By splitting the network devices and systems into smaller groups of devices, you reduce the size of your broadcast domains in the network, reducing unnecessary traffic and improving network performance. It also becomes very easy to apply Quality of Service (or QoS) rules to the network to prioritize latency sensitive or high priority traffic.
Adding Another Layer of Security
Network Segmentation is not a turnkey solution to prevent threats against you or your business. However, it is an important layer in the security controls of your environment to help minimize the efficacy of an attack and provide time to detect and respond to the attack before damage can be done.