IT Services and Fiber Network Provider
The IT Services Provider In the Upper Midwest that Operates its Own AI-Ready Fiber Network
WIN Technology® Services and Solutions
IT Services, Fiber Network and Data Center Solutions for Your Business
WIN Technology has a proven track record of caring about our customers’ success as much as they do, sometimes even more. Whether we’re delivering Managed IT services, providing AI-ready Fiber Network solutions, or leveraging our vast Regional Edge Center capabilities, you can count on WIN for the responsiveness and accountability you need to keep your business running smoothly.

Who We Are
Your comprehensive Upper Midwest technology solutions provider
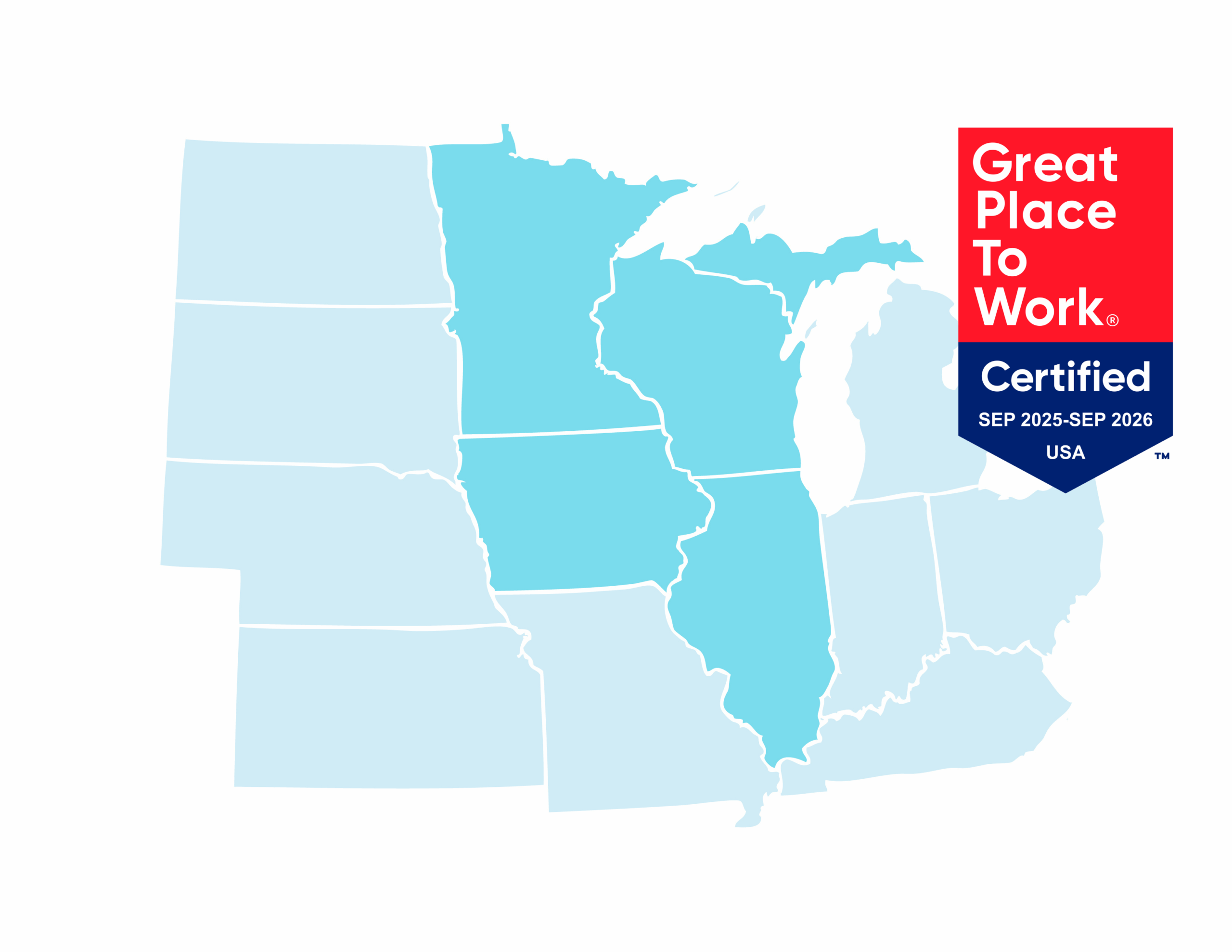
We serve customers in Wisconsin, Minnesota, Iowa, Illinois and upper Michigan and are proudly recognized as a certified Great Place To Work ©.
WIN Technology is the only managed IT services provider in this region that also owns and operates a fiber network across the region. Fast, secure and scalable, our network is designed for low latency and diversity, ensuring uptime and optimal performance.

SUCCESS STORIES
Accelerating Improvements to IT Projects and Systems
A Midwest based insurance agency with a fully staffed IT team was welcoming a new Chief Executive Officer. The CEO wanted to evaluate the organization’s IT infrastructure and organizational competencies and implement a cohesive IT strategy aligned with the vision, missions, and goals of the overall organization…

Working With Us
What to expect from a strategic partnership with WIN Technology

Understanding Fit
Our process is collaborative from the start. As we discuss your expectations, we communicate openly, and we keep the promises we make.

Understanding Needs
Through our discovery process, we seek to build an accurate understanding of your needs so that a sound and mutually understandable promise can be made.

Right-Sizing the Effort
The elements of your proposal are refined as your needs become clear. This ensures alignment on the anticipated value of what we commit to deliver to you.

Proving Competency
As we engage in the project, we monitor and discuss status, performance, changes and improvements through our established delivery and communication practices.

Partnering for the Future
Throughout our partnership, as we keep the promises we have made to you, we enrich the value of services with a continuous focus on practical next steps.
Resources
Explore digital infrastructure ideas and solutions
-
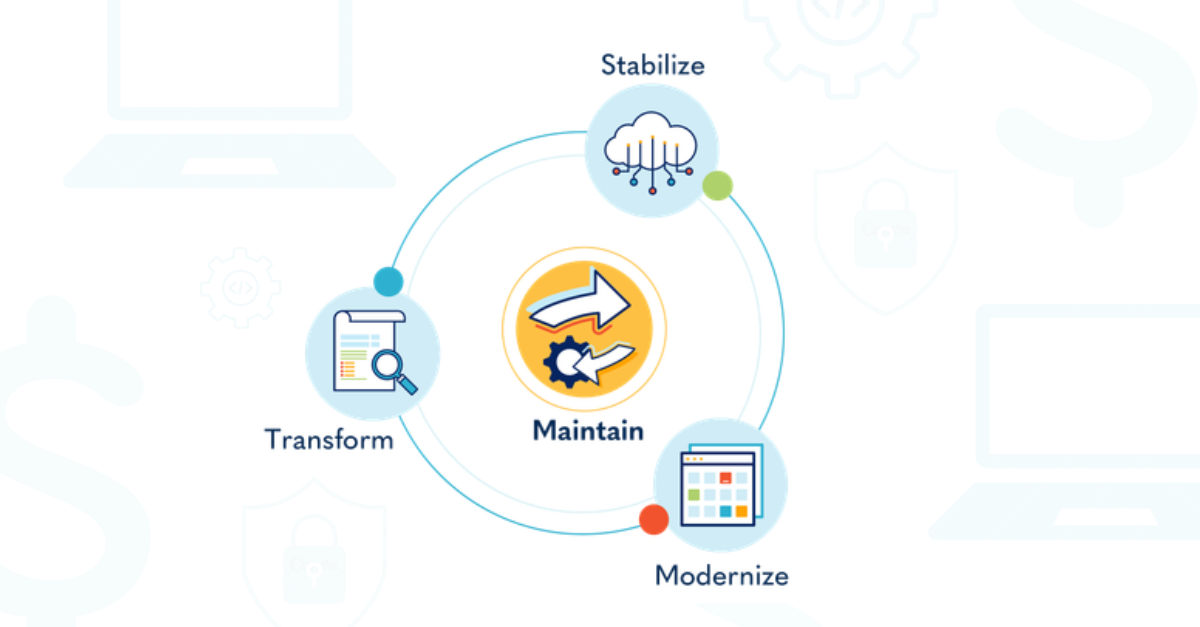
How the Technology Lifecycle Can Help You Attain Business Value
Businesses are constantly changing. Sometimes the use of technology leads, and other times it lags. To attain targeted business value…
-

5 Essential Cybersecurity Projects for Winter
As the days grow shorter and we spend more time indoors, winter offers a chance to focus on projects that…
-

Building a Safe, Structured Path to AI Adoption
Artificial intelligence (AI) is no longer a futuristic concept—it’s already transforming how organizations operate.

